How Physics Helps Lift the Lid on Online Extremism
Neil F. Johnson
Several companies will soon be launching satellites aimed at bringing Internet access to every possible place on the planet. Even before that happens, approximately half the world’s population (~3 billion people) are already using social media, with the dominant platform being Facebook. Each Facebook user is typically a member of more than one Facebook group and a follower of more than one Facebook page. Facebook and its international competitors such as VKontakte (www.vk.com), purposely design their online features to help bring together people into relatively tight-knit clusters so that they can focus on some shared interest or purpose, e.g. jazz fans visiting Washington D.C. But such online clusters can be used for bad as well as good. They can bring together people who are against science, e.g. against vaccination programs. They can also serve to aggregate individuals with a potential interest in extremism or hate against a particular sector of society, e.g. individuals who are anti-immigration or anti-Semites. There are plenty of recent examples where online narratives helped incite individuals to commit violent acts — from Charlottesville, Parkland, Orlando, Maryland, Washington D.C., Pittsburgh and Tallahassee through to Manchester, London and mainland Europe. Detecting who among the 3 billion online users will ever carry out a real-world attack, sounds like looking for a needle in a haystack — but is actually worse since prior to any attack each ‘needle’ may be effectively indistinguishable from any other straw of hay.
In Physics terms, this new online world is one of the largest and most complex ‘many-body’ system in existence. It is far from equilibrium. It has many interacting particle types (i.e. humans, algorithms, bots) that can now interact instantaneously through a complex online web, and with interaction strengths that are independent of spatial separation. It features particles (i.e. people) that don’t do the same things under the same circumstances and are adaptive. And it is a system that is continually being perturbed by a shifting environment of news, rumors, presidential tweets and other world events.
But it is precisely because of this that Physics can provide new insights into its understanding. Starting with an article in Science in 2016 and subsequent papers in Physical Review, our research has shown that the key ingredient in the evolution of online extremism lies in the particular many-body correlations that define these tight-knit online clusters — in particular, the online pages and groups. Though media attention has focused on lone-wolf narratives, and it may very well be that a single individual carries out such an attack, such individuals are likely to have had some prior online exposure to pro-extremist narratives through access to these clusters (i.e. pages and/or groups). So, the correct focus for understanding future attacks likely lies in these cluster dynamics. After all, any physicist knows that it would be wrong to pin the boiling of water on what a single water molecule is doing, or on isolated molecules scattered across the system. Instead the answer lies in their many-body behavior, specifically the clustering of correlations. In the everyday world, taking apart every single car on the planet would never help you explain how clusters of drivers interact to cause traffic jams, or why traffic jams emerge universally in large cities.
Indeed, this message about the importance of developing a physics perspective on this problem, now seems to be resonating outside of physics to other disciplines and also policy-makers. Despite the tendency of the media to focus on ‘lone wolf’ actors, social scientists are now coming round to agree with this collective view (see B. Schuurman et al. (2018) End of the Lone Wolf: The Typology that Should Not Have Been, Studies in Conflict & Terrorism, DOI: 10.1080/1057610X.2017.1419554).
Our journey along this research path started in 2014, when we set out to study the many-body dynamics of pro-ISIS online support. We found that Facebook rapidly shuts down such pro-ISIS groups, but its overseas competitors can be slower to act, probably because doing so would require significant amounts of resources and time. The most important among these is VKontakte (www.vk.com) which has more than 350 million users spread across the world, but which is physically based in the politically sensitive area of Central Europe near ISIS’ major area of operations. Our study of freely available, open-source information on VKontakte between January 1 and August 31, 2015 revealed an ultrafast ecology of 196 pro-ISIS groups1 that share operational information and propaganda, involving 108,086 individual followers. Although these online groups are typically shut down by online moderators within a few weeks of being created, we found that their members would simply go on to form another online group or join an existing online group that was still evading shutdown. And remarkably, all of this information is freely available, because these online groups need to attract newcomers and recruits, and hence their need for openness tends to outweigh any risk of capture. There had been competing research work focusing on analyzing extremism though messaging on Twitter, with the aim of identifying influential online individuals. However, such individual-level approaches met with only limited success from a security perspective, in part because removing the individual ranked No. 1 from any extremist network automatically leads to the individual ranked No. 2 becoming ranked No. 1, then the individual ranked No. 3 becoming No. 2, etc.
Membership of these pro-ISIS online clusters changed on a daily timescale during our study. On the most active day, the total number of follower links reached 134,857 since individual followers can become members of many separate groups. This process of data collection, analysis and modeling provided us with a living road map of online pro-ISIS activity. The high-resolution aspect of our data also meant that this study moved beyond the current focus of the network science field on identifying group structure in time-aggregated networks. Instead, we could see followers’ behavior in real time down to a timescale on the order of seconds. It also moved the understanding of human dynamics beyond the current focus on quasi-static links related to family or long-term friends, toward operationally-relevant dynamical interactions.
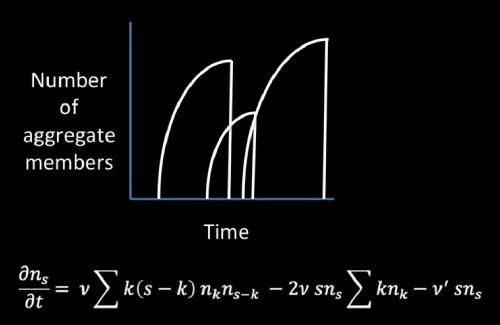
Example of the online group size (i.e. number of members in an aggregate of users) as time increases, for three example online groups (i.e. clusters). Below it, is the equation that correctly describes these online cluster dynamics within a so-called mean-field approximation.
We were surprised to see that the evolution of this online group ecosystem resembled dynamical processes that had been observed in physics (e.g. polymers). However, unlike physical systems where individual units might break off from a group of molecules, or a group of molecules might break into a few pieces, we found that the fragmentation of these online groups is like a shattering process reflecting the sudden moderator shutdown of an online group. Upon deeper analysis, we noticed that the evolution of this online group ecosystem follows a rather precise mathematical form. As the size — i.e. the number of members — of each online group evolves over time, it produces a shark-fin shape as shown in the figure. It is the same shark-fin shape we find in the natural sciences when groups of interacting objects (particles, animals) follow a process of so-called ‘coalescence and fragmentation’. In other words, these online groups of ISIS supporters come together (coalescence) and break up (fragmentation) like fish in schools or birds in a flock might. There’s one difference, though. When they break up, they fragment completely because some external, anti-ISIS entity or online moderator has shut them down. That’s why you see the abrupt drop-off like the edge of a shark fin. This identification of a specific process governing the ecology of these online groups, enabled us to then write down a set of coupled mathematical equations to describe their evolution (see figure above). Solving this equation yields a distribution of group sizes which is essentially the same as that observed in the data, as well as reproducing their characteristic shark-fin shapes in time. We also identified new evolutionary adaptations that these pro-ISIS online groups have managed to invent and adopt. Some may go invisible for a while, and also occasionally reincarnate, appearing at a later date with a different identity and yet managing to retain most of their members. So just as Darwin predicted for biological evolution, pro-ISIS support has adapted to exploit features afforded by its new online environment (i.e. social media website) in order to survive longer.
There are many practical consequences of these findings. Identification of the online group coalescence-fragmentation mechanism suggests that anti-ISIS agencies can step in and break up small online groups before they develop into larger, potentially powerful ones. If anti-ISIS agencies aren’t active enough in their countermeasures, pro-ISIS support will quickly grow from a number of smaller online groups into one super-group. It also warns that if online-group shutdown rates drop below a certain critical value2, any piece of pro-ISIS material will then be able to spread globally across the Internet — ultimately leading to an Internet arms race. Moreover, we find that the birth-rate of these online groups escalates in a particular way ahead of real-world mass onslaught, just as clusters of correlations begin to proliferate ahead of a phase transition in a physical system, such as water boiling — except this is now a dynamical phase transition in time. The important role of these online groups also ties in nicely with earlier work that we did on guilds in the massively parallel online game World of Warcraft3. Furthermore, it means that instead of having to sift through millions of Internet users and track specific individuals through controversial profiling techniques, an anti-ISIS agency can usefully shift its focus toward open-source information to follow the relatively small number of online groups in order to gauge what is happening in terms of hard-core global ISIS support. As for the future, even if pro-ISIS support moves onto the dark net where open access is not possible, or if a new entity beyond ISIS emerges, these findings should still apply since they appear to capture a basic process of human collective behavior. Independent of cause, we can assume that the same types of many-body coalescence-fragmentation phenomena will arise.
For the next steps in this work, we are now carefully teasing apart the composition of these online groups, to find what differences they exhibit apart from their size — and what might make certain groups more influential than others. As part of this study, we have begun to look at characteristics such as gender. This is relevant since we find that about 40 percent of all users in these online groups declare themselves as women. The role of women in extremist activity has become of particular interest recently. For example, in 2016, three women were arrested in Paris for attempting to detonate a car bomb outside Notre Dame Cathedral. “If at first it appeared that women were confined to family and domestic chores by the Daesh terrorist organization, it must be noted that this view is now completely outdated,” François Molins, a French prosecutor, told reporters in announcing the arrests. Molins used the French term in referring to ISIS.
We were surprised to find that in the online pro-ISIS groups, the women tend to act as a far stronger “glue” than men in terms of holding the network together, despite women being in the minority. In the language of social networks, this means the women possess a “higher betweenness.” They provide a disproportionately richer resource for conflict resolution within the network, as well as providing better conduits for propaganda, financing and operational information. In plain terms, the women effectively hold the key to the flow of information, ideas and material between members within the group.
The following diagram shows what having “high betweenness” means for a representative portion of these networks in which men are the majority (M1, M2, M3 and M4) and there is one woman (W). Remove anyone from this portion, other than the woman, and all other members still remain connected. But remove the woman and this portion becomes fragmented. Thus, if you are a man in the network, you could not possibly reach all the other men without the woman being present. The connections between the men, who form the majority population, therefore, rely on the women — who are in the minority.
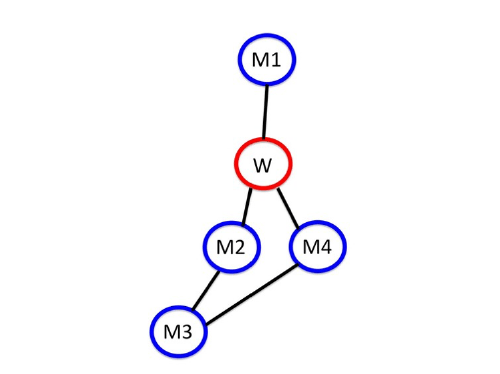
Example of a portion of the network showing one woman (W) and four men (M1, M2, M3 and M4). The woman has a higher betweenness than any of the men, which means that she acts like the glue holding the network together.
Specifically, our results suggest that any given woman will be a conduit for at least twice as many pieces of information, know-how and materials than a man on average. We have also found that the women simultaneously manage to maintain fairly low profiles. This turns out to be favorable for individual survival given the individual risks involved in such extreme activities. The lifetime, or resilience, of an online group of pro-ISIS followers faced with continual shutdowns by the online moderators tends to increase as the ratio of women to men increases. Such a result is consistent with women’s tendency to be better embedded in the network. One practical consequence of our findings is that a sensible way of dealing with a terrorist network would be to engage with the women involved. This is true even if the women are in the minority and also may not currently be deemed key figures.
Of course, much remains to be done. Every day, there are undoubtedly individuals online developing the intent and capability to carry out further violent attacks. So how might a many-body physics theory help detect them before they act? Suppose you meet someone in your university and are interested in knowing the next-step in their career. But instead of asking them their current thoughts and getting a potentially vague answer since they themselves may not yet know, you simply ask them what courses they have taken so far. This will then tell you the spectrum of things that they have been exposed to, and hence you can narrow down what job they will likely end up in — perhaps better than they themselves could at that stage. In an analogous way, such generalized many-body physics models, in the hands of security specialists, could play a similar role for terrorism, extremism and hate by seeing which individuals have passed through which groups and hence likely have the necessary intent and capability. Certainly not a perfect solution, and definitely unconventional, but arguably better than waiting until they do something.
[1] N.F. Johnson et al. “New online ecology of adversarial aggregates” Science 352, 1459 (2016)
[2] Z. Zhao et al. “Effect of social group dynamics on contagion”, Physical Review E 81, 056107 (2010)
[3] N.F. Johnson et al. “Human group formation in online guilds and offline gangs driven by a common team”, Physical Review E 79, 066117 (2009)
[4] P. Manrique et al. “Women's connectivity in extreme networks”, Science Advances 2, e1501742 (2016)
These contributions have not been peer-refereed. They represent solely the view(s) of the author(s) and not necessarily the view of APS.
